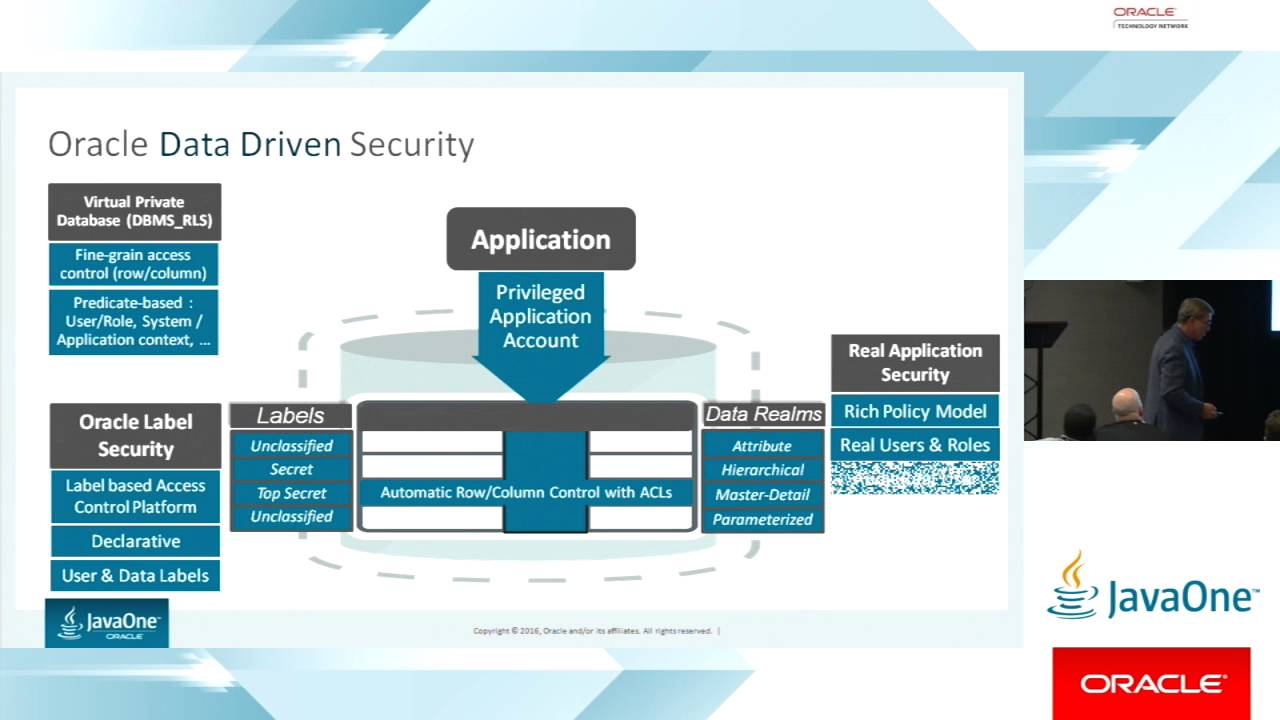
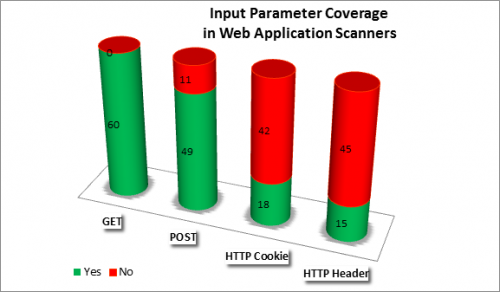
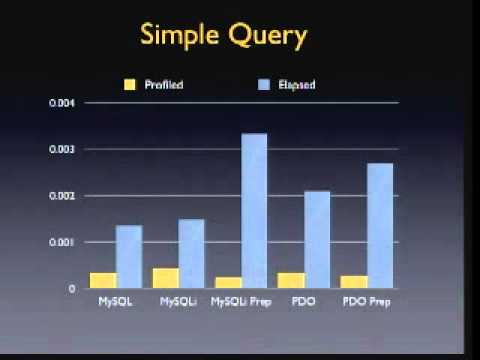
NoSQL Fight for Security
The NoSQL ecosystem thrived on combining scalability and simplicity. That often meant taking short cuts around security and this legacy is still haunting many products. This talk uses Elasticsearch as an example and covers both the technical background as well as anecdotal evidence of past incidents. Finally, we also discuss …