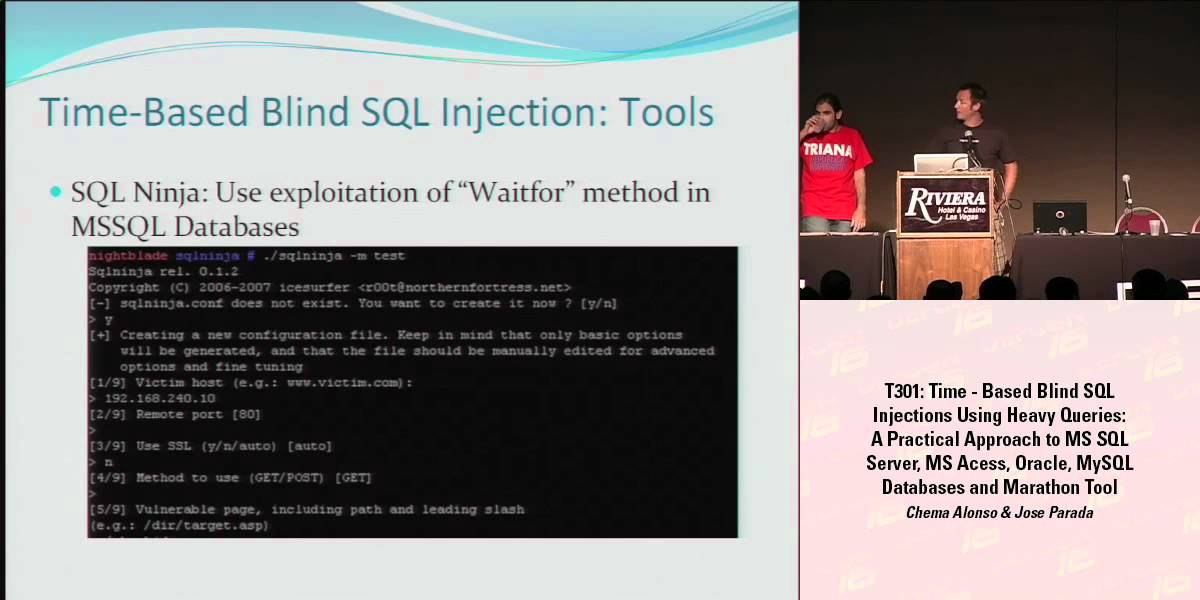
Advanced MySQL Exploitation
This talk focuses on how MySQL SQL injection vulnerabilities can be used to gain remote code execution on the LAMP and WAMP environments. Attackers performing SQL injection on a MySQL platform must deal with several limitations and constraints. For example, the lack of multiple statements in one query makes MySQL …